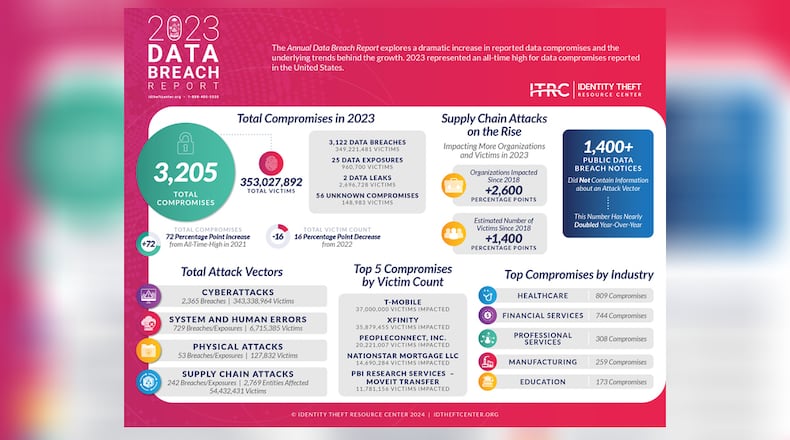
“2023 was a watershed year for publicly reported data compromises, ironically during the 20th anniversary of the first data breach law,” said James E. Lee, chief operating officer of the resource center. “In fact, there were more data breaches caused by cyberattacks last year, 2,365, than the previous record for all types of compromises in a single year, (which was) 1,860 in 2021.”
One of the largest data compromises in 2023 involved the cyberattack on MOVEit, a file transfer software tool owned by Progress Software, that impacted a wide variety of companies and organizations, including Dayton-based CareSource and Premier Health.
As of Thursday the resource center had identified 1,417 organizations or companies impacted by the MOVEit breach, with an estimated 72.7 million victims.
Clients and customers of CareSource and Premier Heath whose information was possibly compromised were notified and offered credit monitoring. Both local companies are among multiple companies being sued in federal court over the MOVEit breach.
Credit:
Credit:
Late last year Mercy Health, which operates the Springfield Regional Medical Center, announced a different breach, which involved hospital system vendor Perry Johnson & Associates, Inc.
CareSource spokesman Joe Kelley, Premier Health spokesman Ben Sutherly and Mercy Health spokeswoman Maureen Richmond all declined comment. But Sutherly provided a document from hospital system vendor Welltok, Inc., of Denver, detailing the breach of Welltok’s MOVEit transfer server and its effort to notify impacted individuals.
Richmond provided a document from Perry Johnson & Associates, Inc. indicating that the Henderson, Nevada-based company had alerted people whose information was compromised.
T-Mobile data compromise tops list
The company with the most victims impacted by a data compromise in 2023 was T-Mobile, with 37 million people, followed by Xfinity, with 35.9 million, the report said.
PeopleConnect, Inc. ranked third with 20.2 million victims, and Nationstar Mortgage LLC, doing business as Mr. Cooper, was fourth, with 14.7 million people impacted.
Two companies using MOVEit, PBI Research Services and Maximus, Inc., ranked fifth and eighth respectively, with a combined 22.8 million victims impacted, the report said..
The Perry Johnson & Associates breach impacted 9 million people and ranked ninth.
The health care industry had the most compromises in 2023, followed by financial services, professional services, manufacturing and education, the report said.
Lee said the number of breach notices that did not have actionable information “to help businesses and individuals prepare for similar attacks also grew in 2023, when less than half of cyberattack-related notices included information about what caused the breach.”
While there typically is never just one reason that data breaches increase, Lee said there were several trends in 2023 that help explain the jump in cases.
“Many professional cybercriminals supported by nation/states resumed stealing business and personal information after being more focused on the conflict between Russia and Ukraine,” said Lee. “Professional cybercriminals and nation/state actors focused more on finding and exploiting zero day software flaws.”
In 2023 there were 110 publicly reported zero day attacks, which occur when cybercriminals exploit software flaws that are known but not yet patched. In 2022 there were eight, the report said.
Data compromises like the hack of MOVEit are known as supply chain attacks.
Credit: Contributed
Credit: Contributed
“Cybercriminals are focusing more on supply chains where attacks against a single, less well-defended vendor can give an attacker access to the data of many companies,” Lee said. “(And) generative artificial intelligence is making phishing attacks and social engineering schemes more effective and more successful.”
What are data compromises?
Data compromises include breaches, exposures and leaks.
Nearly all of the compromises in 2023 were data breaches, which impacted 349 million victims.
Breaches are when unauthorized people remove personal information from where it is stored. It sometimes occurs through ransomware attacks, when hackers use malicious software to infect a computer network and demand money from the victim.
Breaches can compromise personal information like Social Security numbers, logins and passwords, credit card numbers, consumer information, and in some cases also expose company data to the cyber intruders.
Two of the data compromises in 2023 were leaks impacting 2.7 million victims. Leaks are instances when information people have put online is scraped from a website. That occurred in past years on the Facebook and LinkedIn social media platforms, according to the center.
Exposures, typically caused by a system or human error, are generally considered lower risk because there is no indication information was accessed, copied or removed. The center found 25 data exposures that put the information of 960,700 people at risk.
Cyberattacks remain the top cause of data compromises, accounting for the vast majority over the past five years, the report said.
While data compromises have increased dramatically, the number of annual victims has declined since 2018, when there were 2.2 billion victims, and 2017, when there were 1.8 billion, according to the center.
Some of the most prominent data compromises those years occurred at Equifax, Starwood Hotels/Marriott International, River City Media, Google, Facebook, Orbitz, T-Mobile, Verizon, and Uber Technologies Inc., according to Lee.
The resource center advocates stronger federal rules to bolster the patchwork of breach notification laws on the books in every state, U.S. territory and the District of Columbia.
California was the first state to require notification, passing a law in 2003 primarily aimed at what was at risk at the time, personal information stored in filing cabinets, thrown in the trash and on computer disks and drives, the report said.
The resource center calls for a uniform definition of personally identifiable information that would trigger a mandatory data breach notice, require that state and federal agencies be notified within 24 hours and that potentially impacted individuals be notified within 72 hours after that.
“The two-decade old legislative and regulatory framework designed to alert consumers to breaches is broken,” said Eva Velasquez, CEO of the resource center. “Businesses under or non-report breaches. We need to bring a level of uniformity to the breach notice process to help protect both consumers and business.”
| Cybersecurity best practices for companies |
|---|
| Train employees in cybersecurity awareness |
| Install firewall and anti-virus software |
| Replace out-of-date equipment and software |
| Immediately install security patches and updates |
| Do frequent and duplicative backups |
| Have a written cyberattack response plan |
| Install a virtual private network |
| Scan emails before they go to employees |
| Change passwords frequently |
| Use multi-factor authentication |
Follow @LynnHulseyDDN on Facebook, Instagram and X.
About the Author